Filters Introduction
A main goal of Cryptbreaker was to build upon existing password evaluation and auditing tools to provide improved features and new functionality with actionable outcomes in mind. Instead of generating static reports we want to provide information that you can explore and use to effect change. It is for this reason that Cryptbreaker provides both reporting and data views. The provided data table view allows for advanced searching and filtering as well as data export.
Filter Types
The data table view can be accessed by clicking the name of any of your Hash Files on the main application page. Once in this view there are two main ways to apply filters to the data presented:
- Through table filters accessed by using the table filter button on the top right of the Hashes table (three horizontal lines)
- Via the search feature accessed by clicking the magnifying glass at the top of the Hashes table
Hash Objects
Regardless of how you apply filters their functionality is based off of the structure and attributes of the ‘hash’ objects stored in the Cryptbreaker database. Included below is a sample hash object:
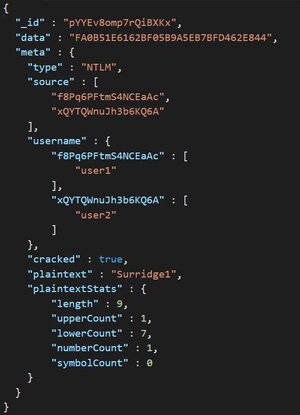
If the plaintext password was located on a breach that the tool is aware of the hash object will include the additional ‘meta’ attributes of ‘breachesObserved’, ‘listCategories’ and ‘lists’ which information around what breaches the password occurred in. These more generic attributes of hash objects are filtered on by using the table filters button. This includes the hash type, whether or not it the hash was cracked, if the password was contained in a breach that Cryptbreaker is aware of, and whether or not the password has been marked as non-compliant with the hash file’s configured policy.
More complex filtering can be performed by using the search bar to perform simple text based searches as well as perform advanced filters. These advanced filters allow for queries focused on specific attributes of hash objects (such as the password length) and also enable filtering across database objects (for example checking to see if a hash is associated to a user who is a member of a particular group).
Advanced filters take the format of filter:object.attribute conditions where object.attribute specifies one of the supported filter fields (ie: user.inGroup to filter for data based on associated user group memberships and password.length to perform filtering based off cracked password length) and the conditionals are specific to the object.attribute that is being queried.
Supported Advanced Filters
Currently the following are supported advanced filters:
password.length
Query for passwords based off their length. Supported queries can use the >,<,>=,<=, or == operator. To look for passwords less than or equal to 6 characters in length you could use: password.length <= 6
user.inGroup
Filter hashes based off groups containing hash. If you wanted to filter for hashes that belong to members of the “Domain Admins” group you could use the following: user.inGroup “Domain Admins”
In order to query on this field you will have to upload group files in the ‘report’ view for the associated hash file.