Quick Password Cracks and Audits
Background
During most offensive engagements, weak passwords and password reuse lead to system compromise. It is for this reason that assessing password strength on a regular basis is key for organizations to factor this information into their overall understanding of risk. From my discussions with students of the SANS SEC460 (Enterprise Threat and Vulnerability Assessment) course, across a wide range of industries and verticals, it seems that password cracking and auditing run into two major roadblocks:
- Organizational capabilities and resources
- Security concerns around compromising credentials
To facilitate my own offensive activities and address both roadblocks, I wrote a tool to perform password cracking using cloud-based resources in an affordable and secure manner, with limited credential exposure. Allow me to introduce you to Cryptbreaker

Cryptbreaker
Cryptbreaker is web application that utilizes Amazon Web Services (AWS) to perform cloud-based cracking of LM and NTLM hashes (the primary storage mechanism for hashes in a Windows Domain environment). Using a cloud-based service allows us to accomplish our goals of affordability, ease of use, and password auditing, without exposing plaintext credentials.
Affordability
It achieves its goal of affordable performance by utilizing AWS spot instances to request powerful cracking machines at a fraction of their regular operational price.
A quick example of this would be using p3.2xlarge instances in AWS to crack NTLM hashes at a rate of 77.5 GH/s for $1 per hour vs the standard rate of $3 per hour (saving 66% over the standard rate). Additionally, the cracking box will self-terminate as soon as cracking and analysis are complete to limit how long the box is actually running for, so you’re only charged for the actual time it takes to perform this analysis.
Ease of Use
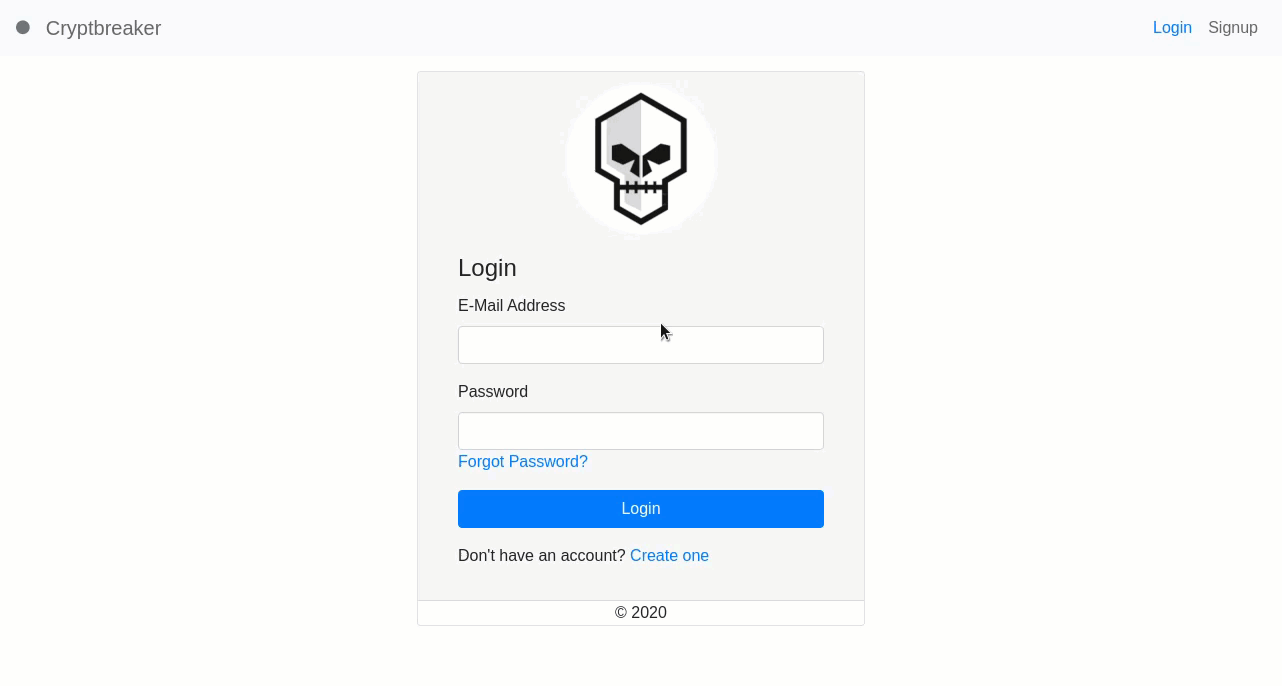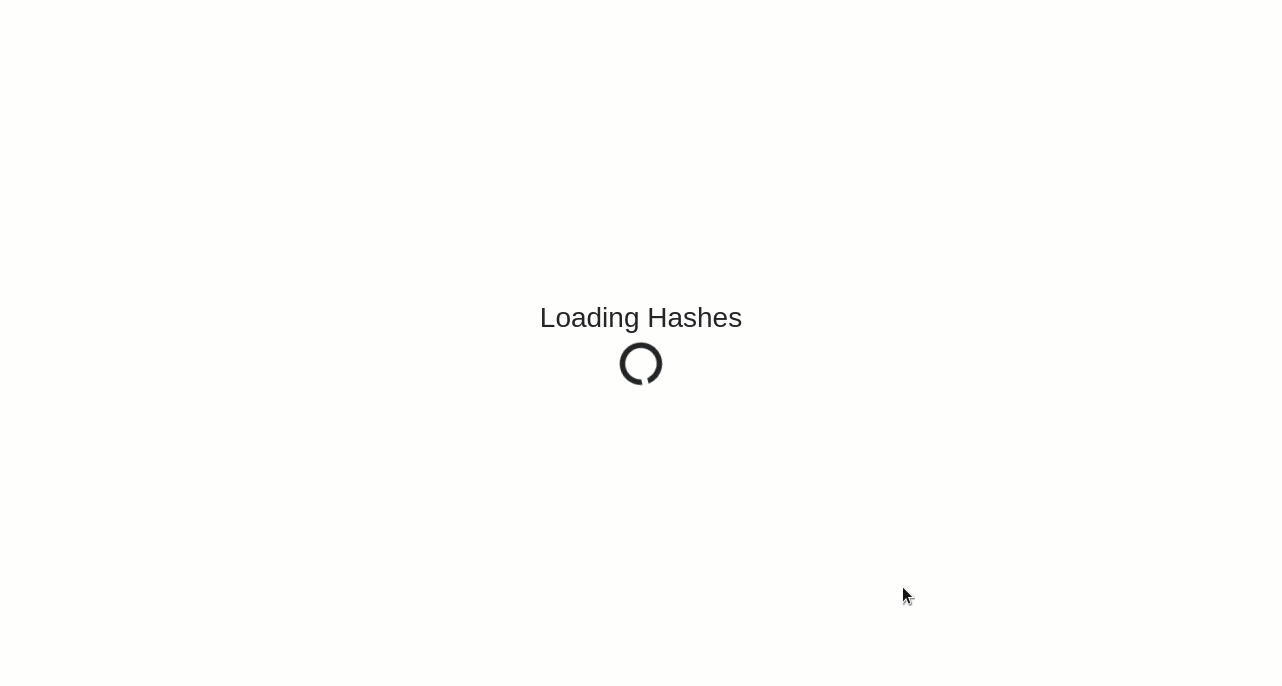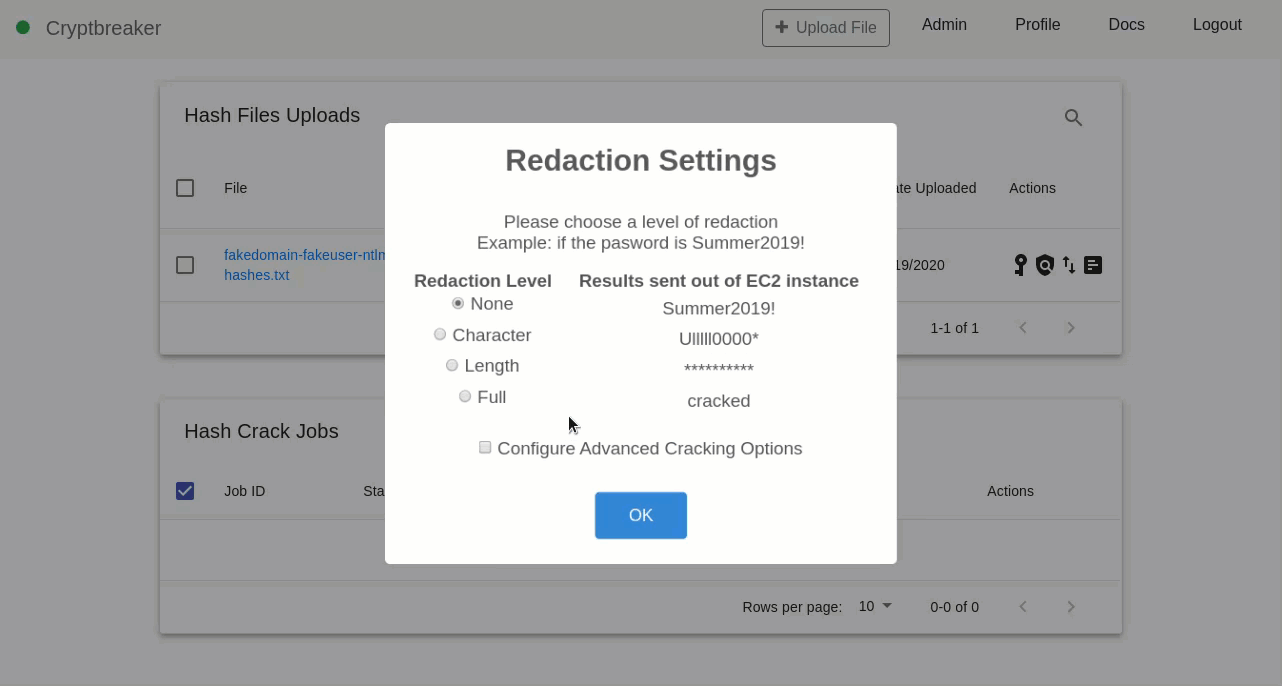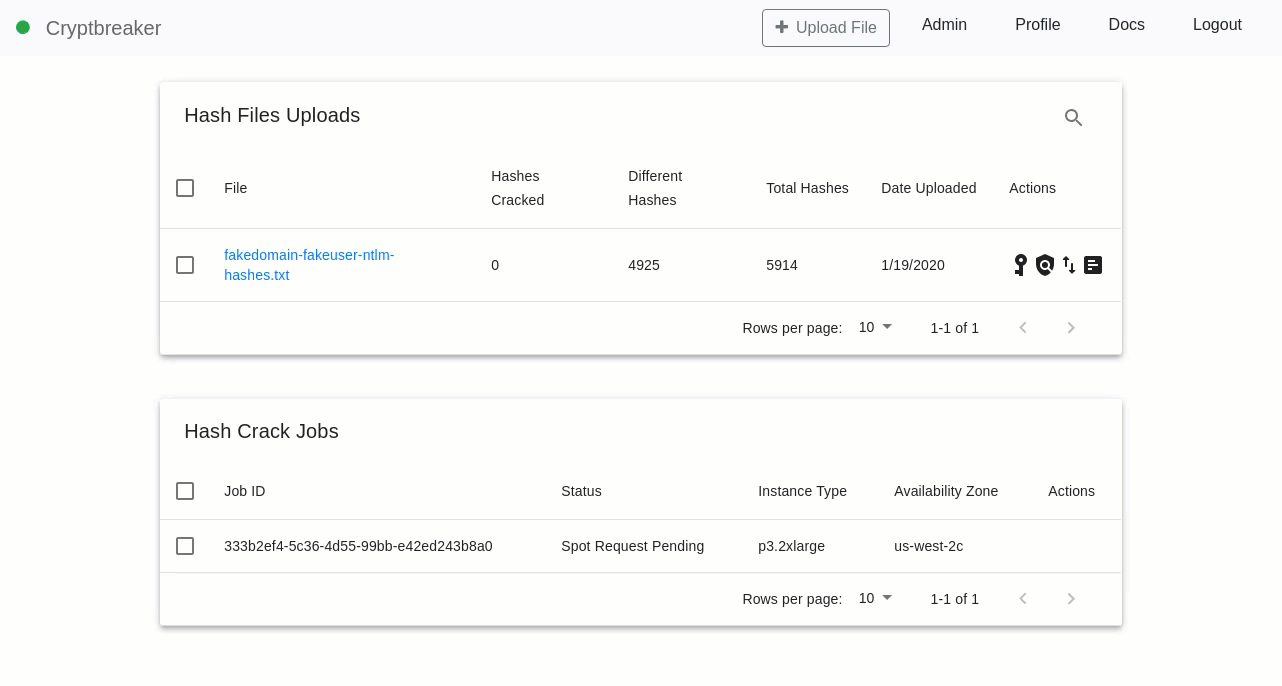
Ease of use is accomplished by allowing a user to upload a list of LM/NTLM passwords to crack (optionally with usernames) via the web UI and then providing a ‘Crack all’ button. That’s it! The tool will automatically provision a new cracking machine in the cloud, install necessary software and drivers, download numerous wordlists and word mangling rules to create a robust list of possible passwords, and perform the cracking.
Security
Security is accomplished by taking advantage of cloud-native features present in AWS to allow for cracking of passwords and crack success statistics calculations without ever sending plaintext passwords between the Cryptbreaker application and the cloud.
This is accomplished by using a private Amazon S3 (Simple Storage Service) bucket (no access from members outside the owning AWS account) to upload hash data only (no usernames or organizationally identifiable information) via HTTPS to a location that the cracking machine is then authorized to pull down and delete the uploaded hash file from S3.
Cracking occurs on the cloud instance, which has no remote access protocols enabled – one of the first things we do when the box boots is disable the SSH service. Once cracking is complete the local copies of wordlists are queried to determine what breaches/wordlists led to password identification and an optional level of obfuscation is applied to the password hashes prior to them being uploaded to the private S3 bucket and the cracking machine self-terminating. The cracked hashes (or masked values) and password list/breach information is then downloaded by Cryptbreaker and local analysis and statistics are performed to provide an analytical view.
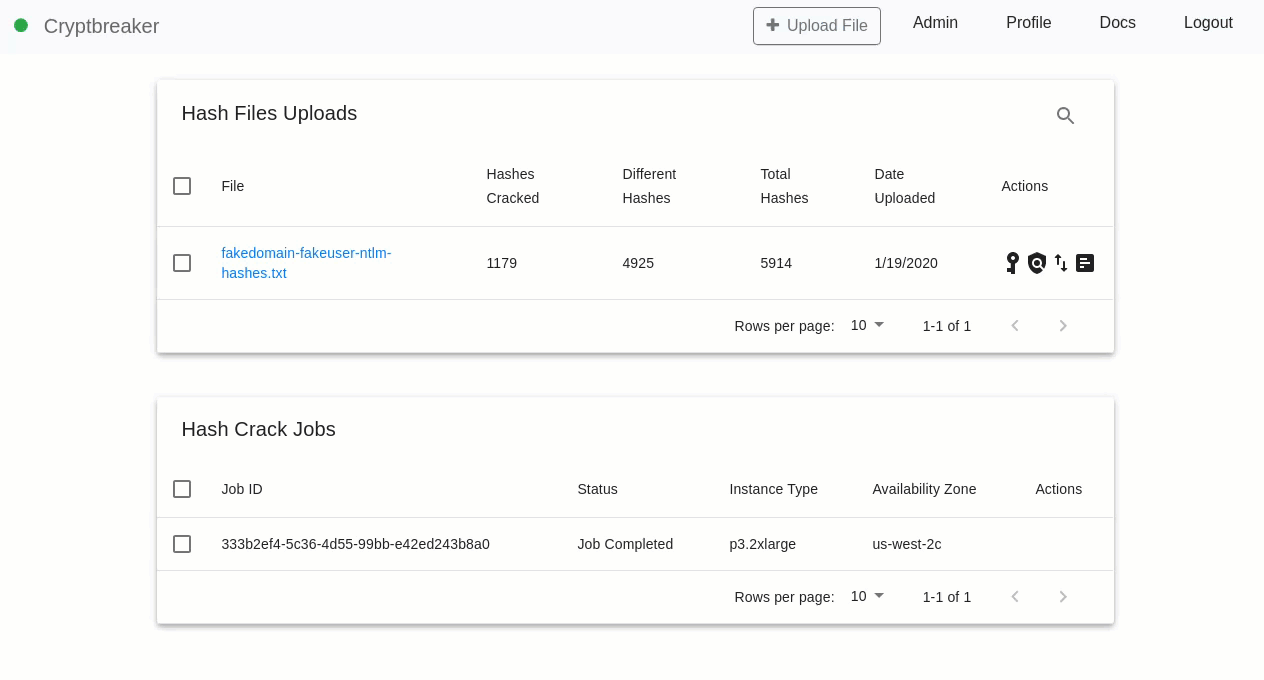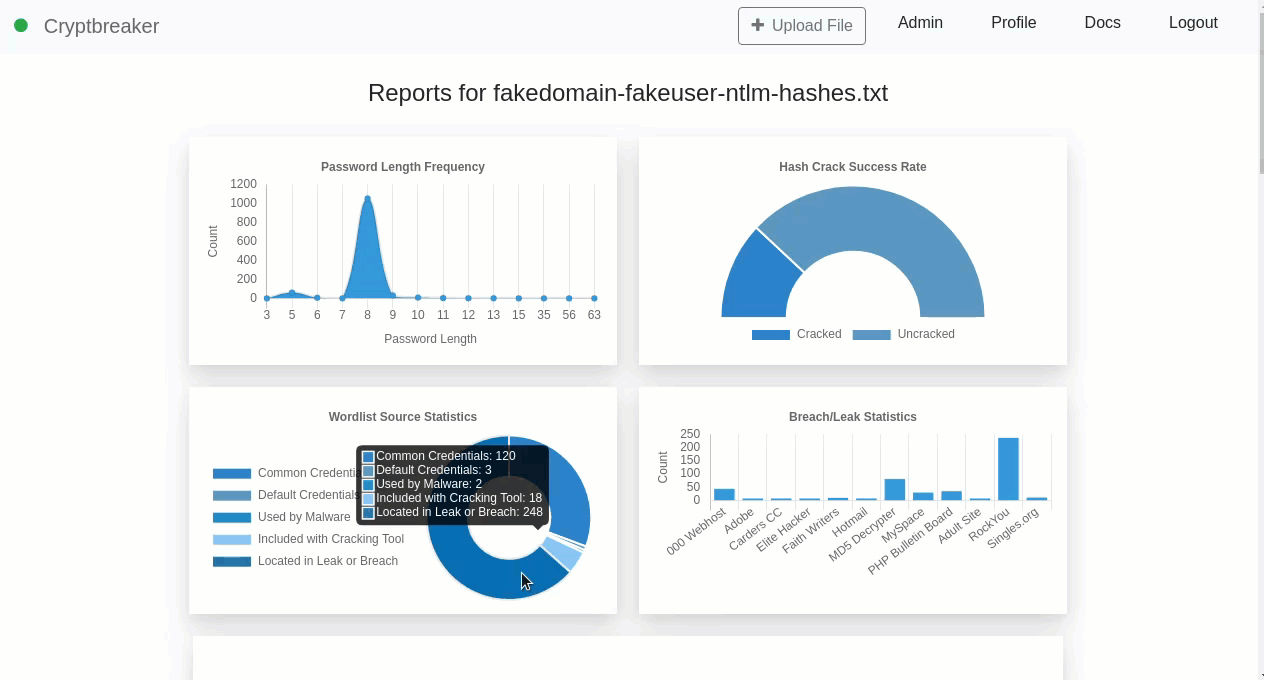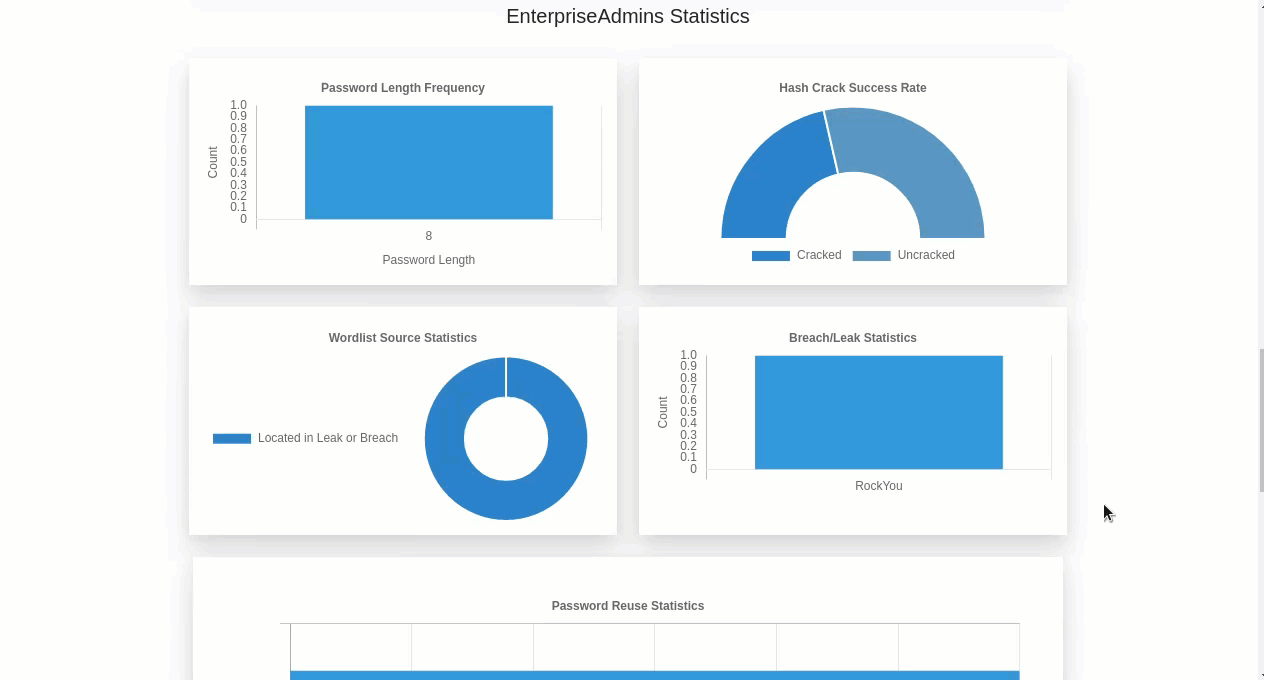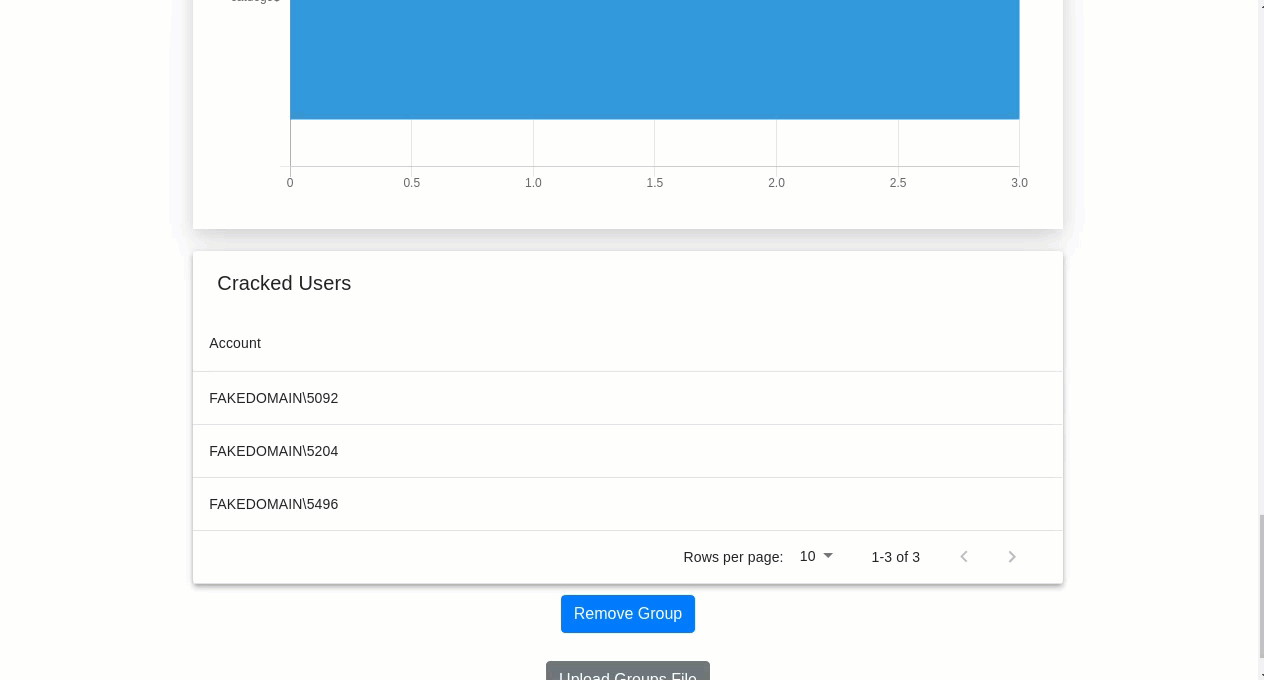
If masking of passwords is performed, then the plaintext passwords never leave the cloud-cracking box but useful information such as password length and reuse patterns can still be identified.
For offensive operations masking doesn’t have to be performed and penetration testers/red-teamers can still receive plaintext credentials if desired.
These are just the main highlights about Cryptbreaker but give the tool a try!
Happy Hacking!