We Haz the API

Release Notes
As usual, lets start with the release notes. The primary focus of the 1.2 release was expose existing Cryptbreaker functionality via API. A secondary purpose was to add support for another hash type that I frequently find myself wanting to crack.
- REST Based API w/Application Tokens
- NetNTLMv2 Cracking Support Added
- Couple of additional Scripts/Tools to get you started using the Cryptbreaker API
Let’s talk about these features in a bit more detail.
We’ve got an API now!
Ok, so this may seem like not such a big deal but for anyone looking to improve automation or integrate with other tools this is a key component of what Cryptbreaker needed to provide. A quick description of setting up your account for API use and an overview of the exposed functionality is covered in this section. For full (and up-to-date) API documentation as well as additional examples see the postman docs
Generating an API Key
The Cryptbreaker API uses token based authentication in the form of an API key. The API key is provided in every request to the API as the Apikey header. To generate this API key, simply navigate to the Profile page of the latest version of Cryptbreaker and click the little plus button on the top right of the API Keys table. Then click the eye icon for your created key to retrieve the value.
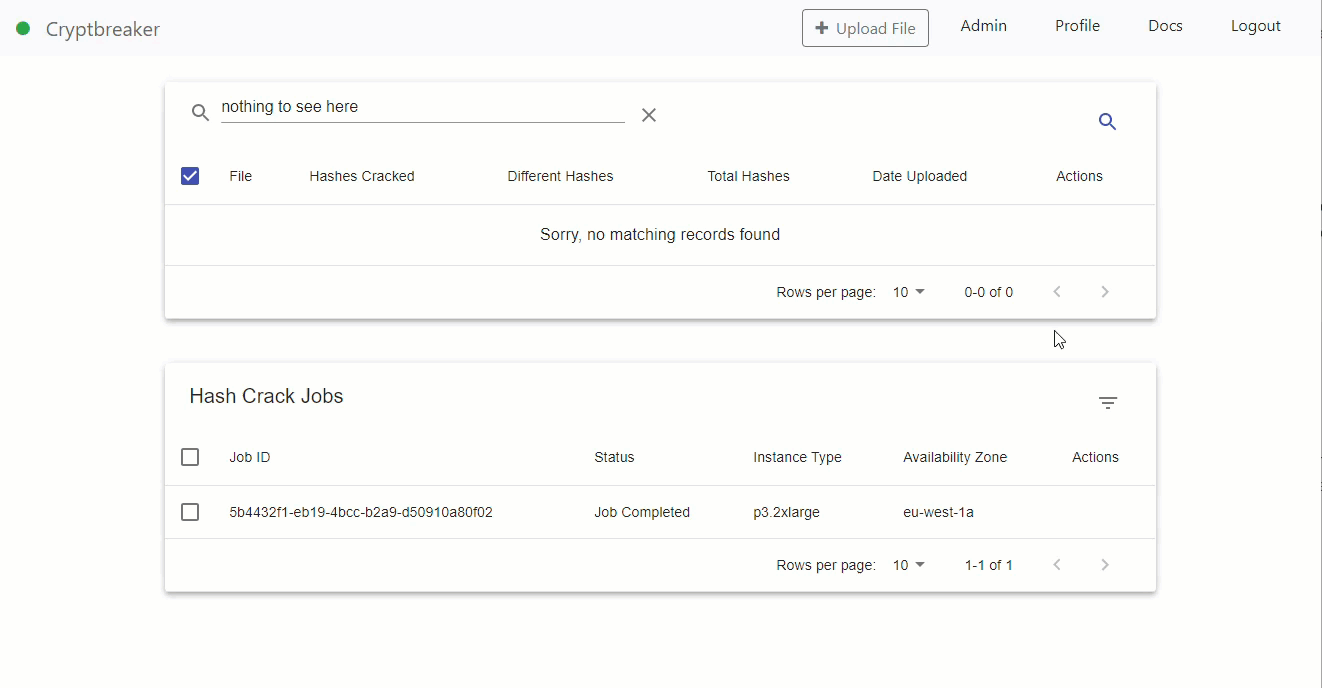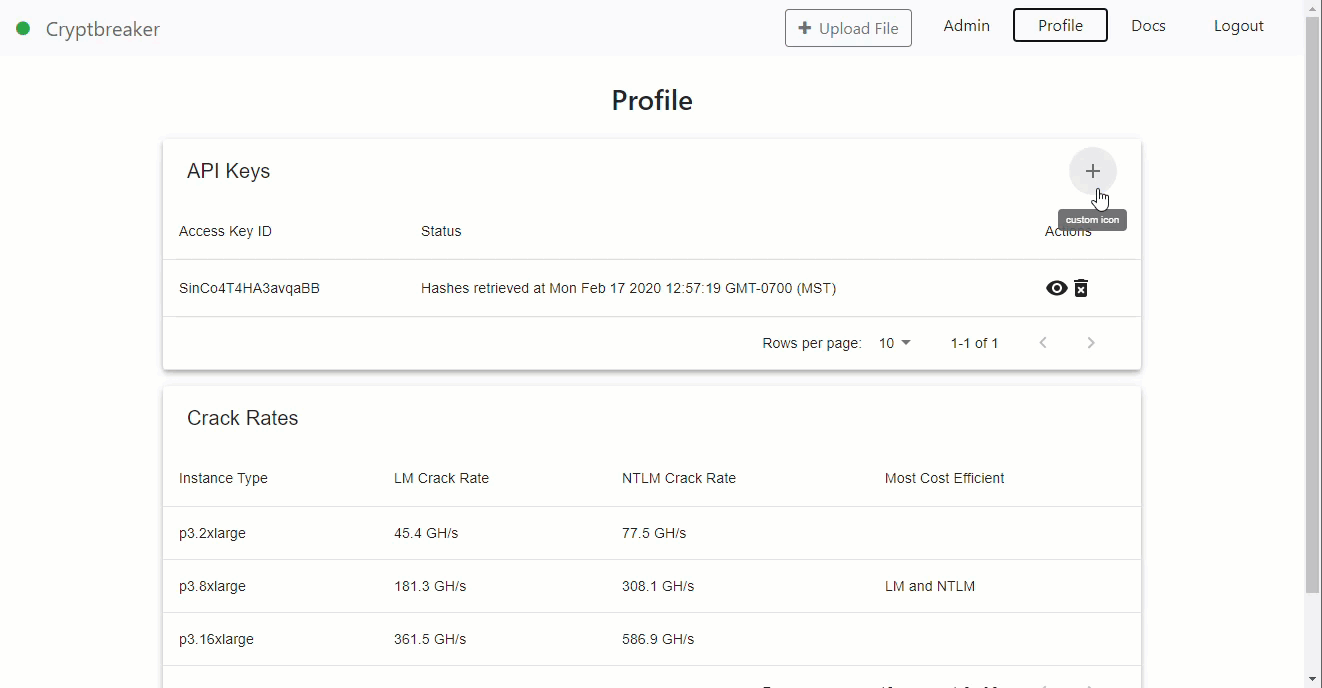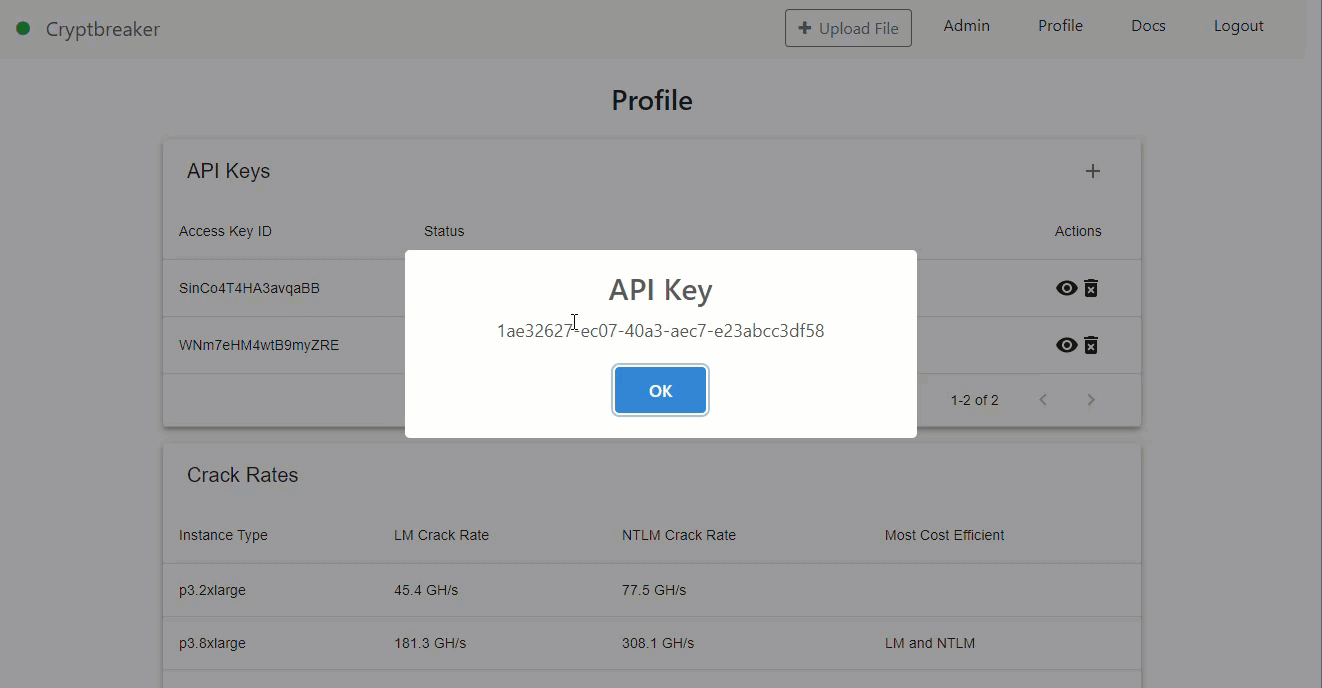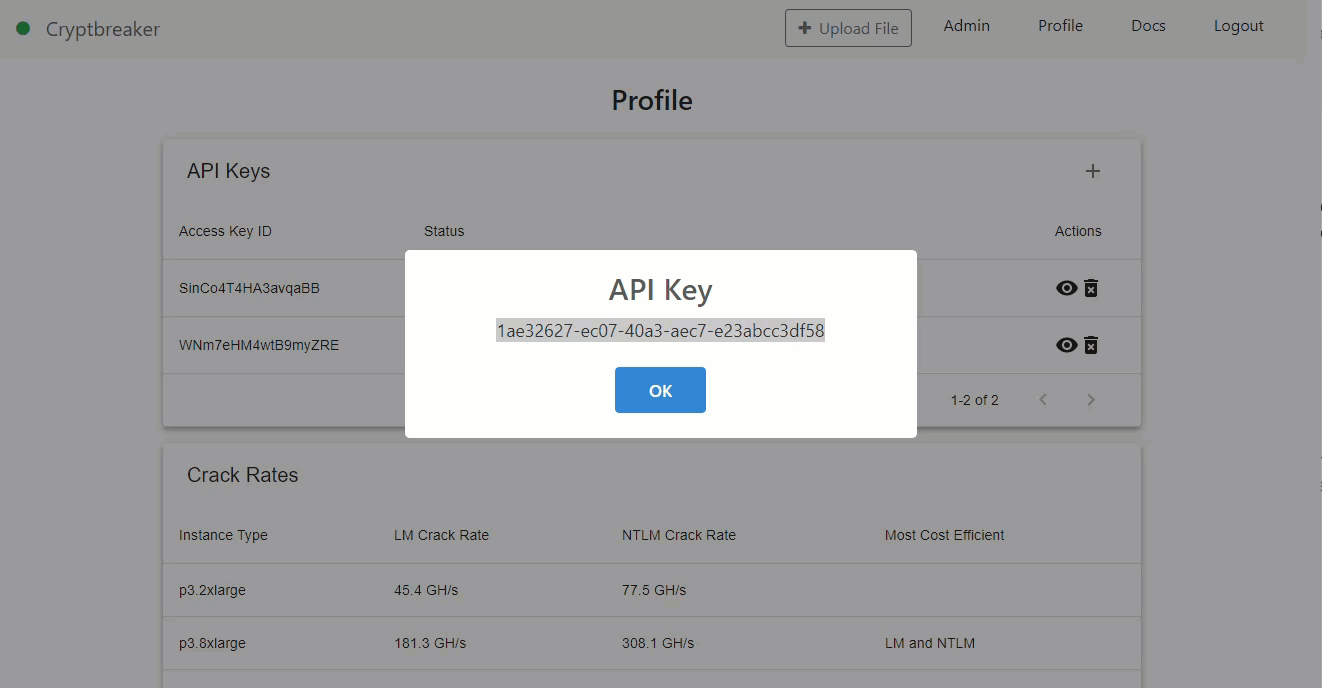
Now that we’ve got our API key what can we do with it? Well the answer is… basically everything you can do in the GUI and more!
The API endpoints published as of this release (broken down by function) are: * File Management * GET /api/files - List all files - Retrieves data that would normally show up on the ‘Hash File Uploads’ table of the main application page * GET /api/files/:fileID - Retrieve file details (includes the calculated statistics used in the reporting tab) * GET /api/files/:fileID/delete - Delete the specified Hash File * Retrieval of Hashes * GET /api/hashes - Retrieve all the hashes that Cryptbreaker knows about * GET /api/files/:fileID/hashes - Retrieve the hashes associated with a particular file * GET /api/jobs/:jobID/hashes - Retrieve the hashes associated with a particular hash crack job * POST /api/hashes/check - Allows you to send hash data to Cryptbreaker to see if it’s already been cracked * Hash Cracking Management * Hash Cracking Awareness * GET /api/jobs - List all hash cracking jobs in Cryptbreaker (what you’d see in the ‘Hash Crack Jobs’ table of the main application page * GET /api/jobs/:jobID - Retrieve details about the specified job * GET /api/jobs/:jobID/status - Retrieve just status for specified job * Hash Cracking Management * GET /api/pricing - Refresh and return the current ‘best’ spot pricing available * POST /api/hashes/ - Allows you to upload hash data as JSON to Cryptbreaker for cracking * POST /api/files/ - Allows you to upload a file to Cryptbreaker as base64 encoded content. This is the same as using the ‘Upload File’ button in the UI * POST /api/jobs/ - Allows you to create a hash crack job for specified file(s) * POST /api/crack/file/ - Convenience function that automates most of cracking for you. Allows you to upload a file to Cryptbreaker as base64 encoded content, then queues a hash crack job and returns the uploaded fileID, the created jobID and an array of any hashes that you just uploaded that had already been cracked. See postman docs for more details * GET /api/jobs/:jobID/pause - Allows you to pause a running job (similar to clicking the pause button in the UI) * GET /api/jobs/:jobID/resume - Allows you to resume a paused job (similar to clicking the resume button in the UI) * GET /api/jobs/:jobID/delete - Allows you to delete a stopped/paused job (similar to clicking delete in the UI)
We’ve got an API… So now what?
In addition to releasing the new version of Cryptbreaker via GitHub and Docker Hub we’re also releasing two PoC tools which utilize the new API. They are a Cobalt Strike Aggressor Script and a PowerShell script.
Cryptbreaker.cna
The first tool that we’ll talk about is Cryptbreaker.cna a Cobalt Strike aggressor script that allows you to crack recovered credentials without ever leaving the Cobalt Strike operator interface. To setup and use just make sure you’ve got a fully configured Cryptbreaker instance running and accessible from your operator system, get your API key, and grab the latest version of the Aggressor Script from my AggressorScripts repo and load it into Cobalt Strike.
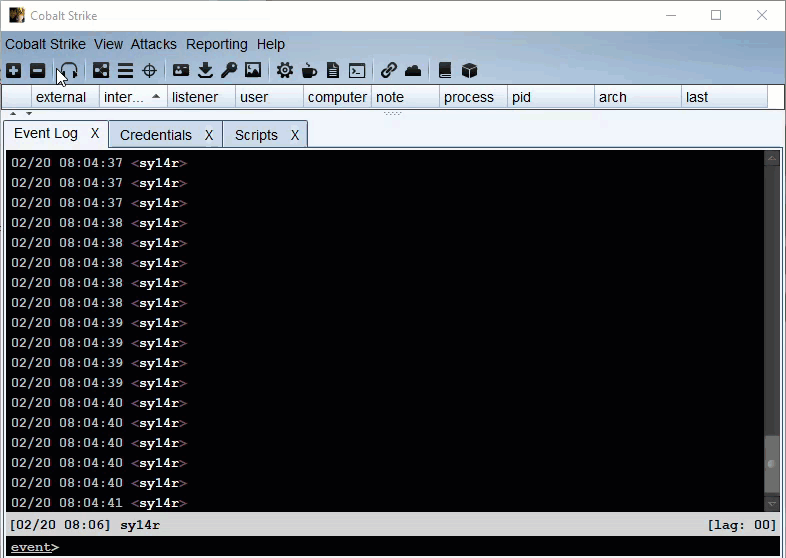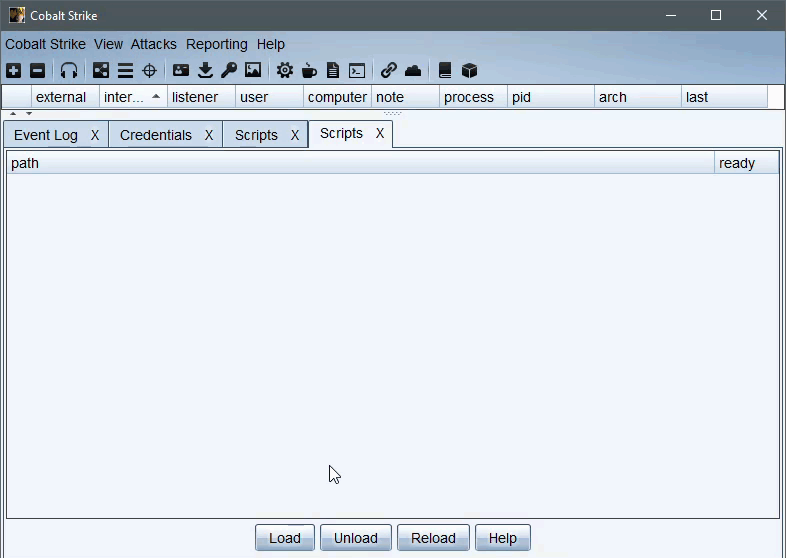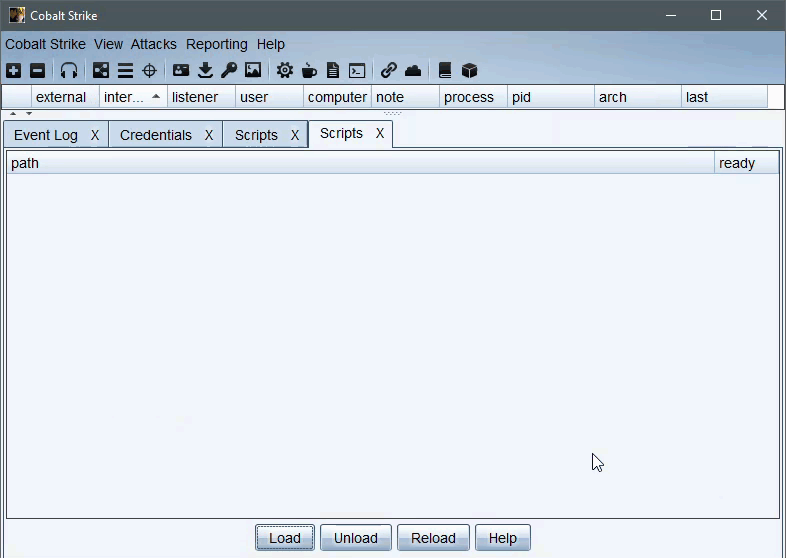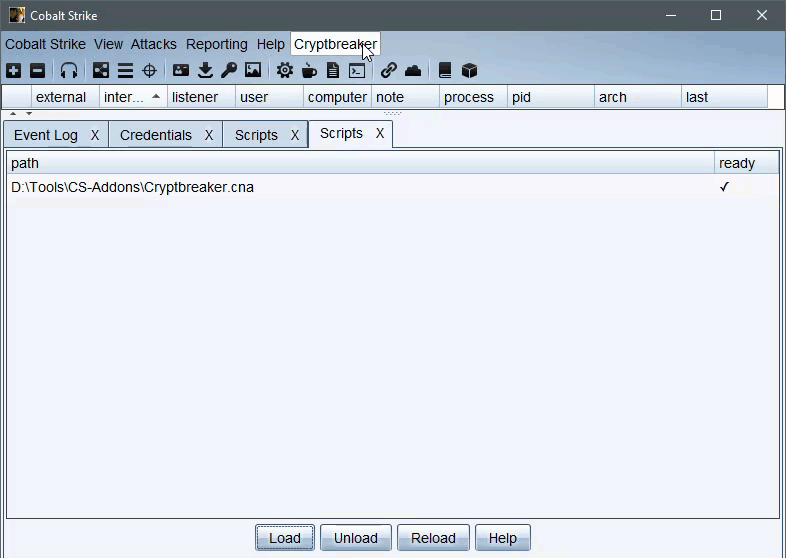
Once the script is loaded you can manage configuration and cracking from the Cryptbreaker menu that has been added to the top menu bar. This menu is where you’ll configure the Cryptbreaker instance connection info and cracking preferences.
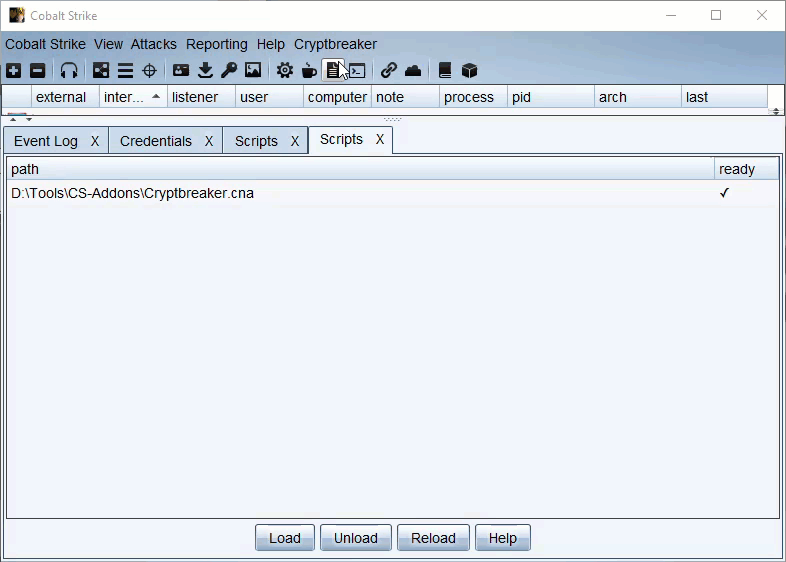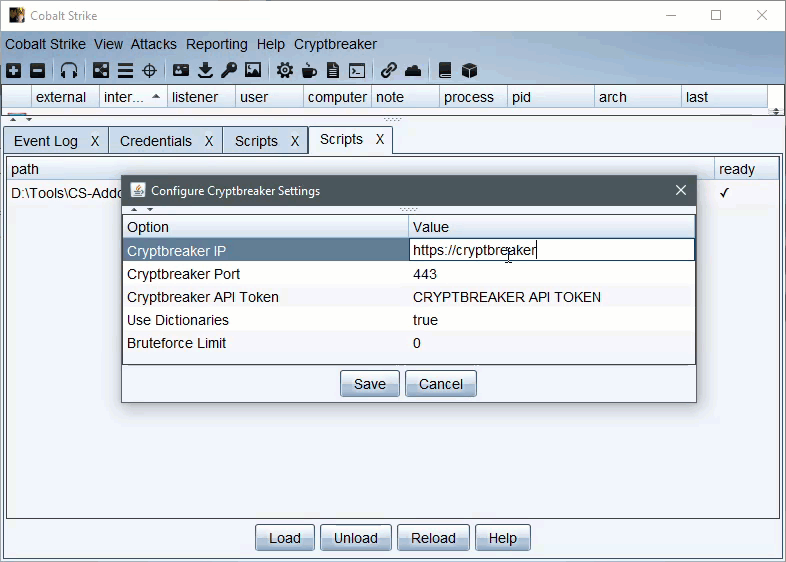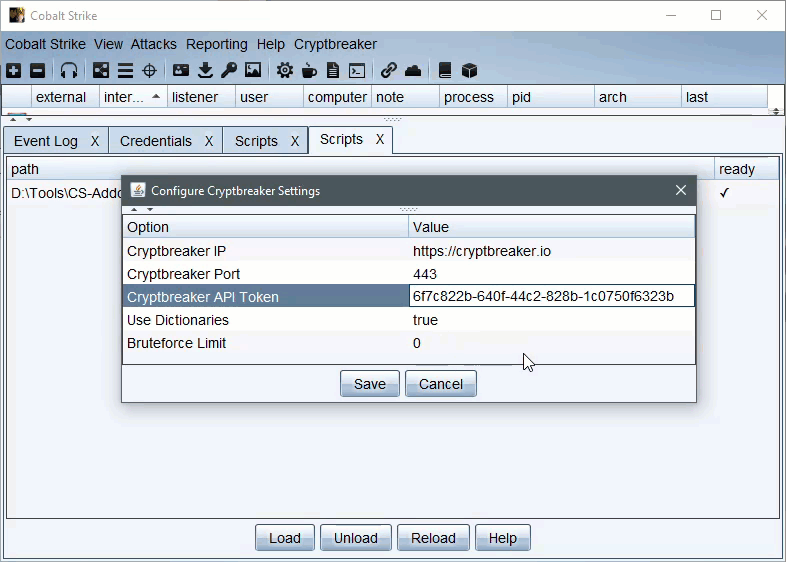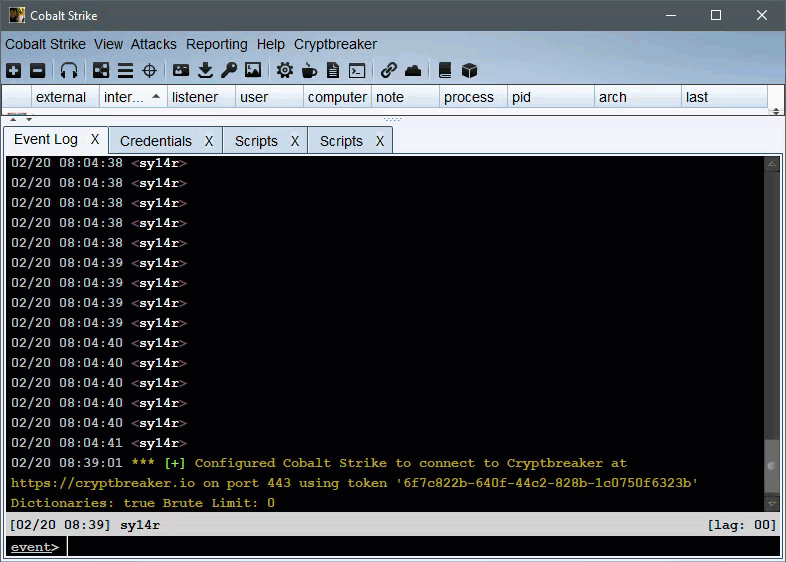
The configuration table specifies the instance URL/Port and API token to use. Additionally the ‘Use Dictionaries’ and ‘Bruteforce Limit’ values will be used to control submitted hash cracking jobs (default is to disable brute forcing and just use dictionaries)
Once Cryptbreaker is hashes can be checked/cracked in one of two ways. You can take actions against ALL current credentials by using the Cryptbreaker menu in the top menu bar to ‘Crack All’ or ‘Check All’ or you can go to the Credentials view and select any number of creds and right click for a context menu to crack or check just the selected credentials.
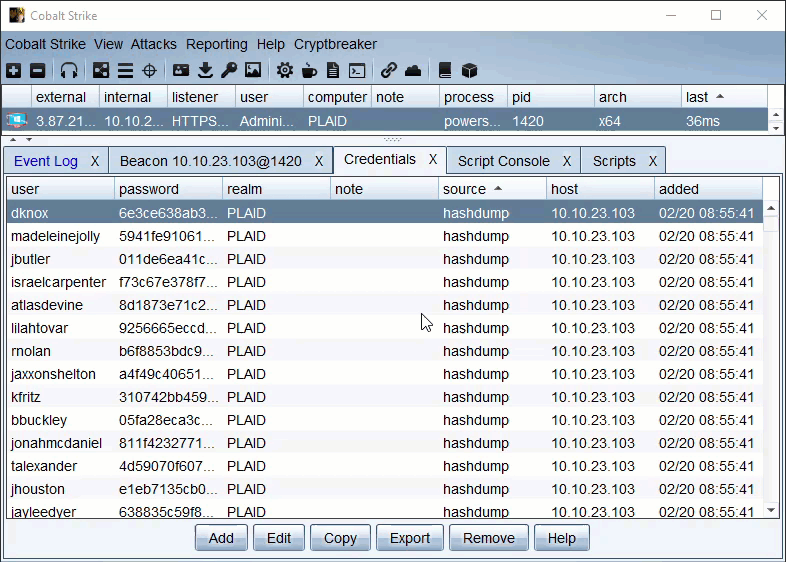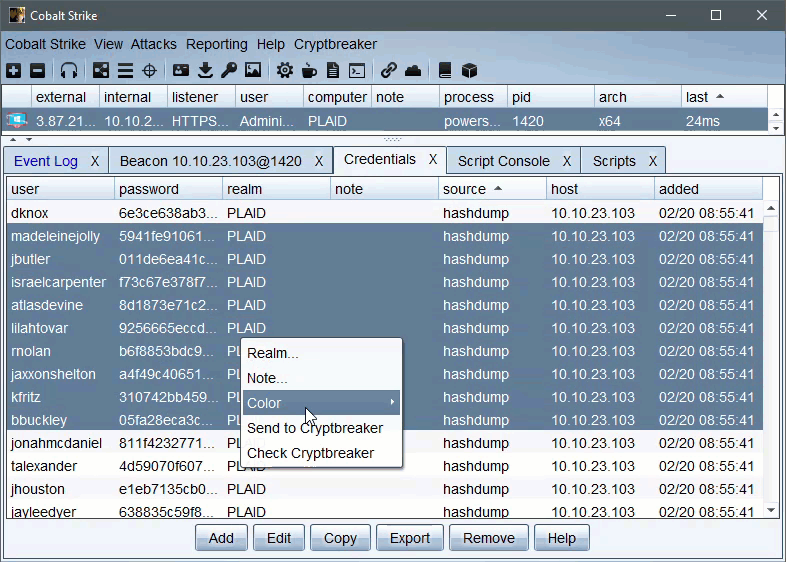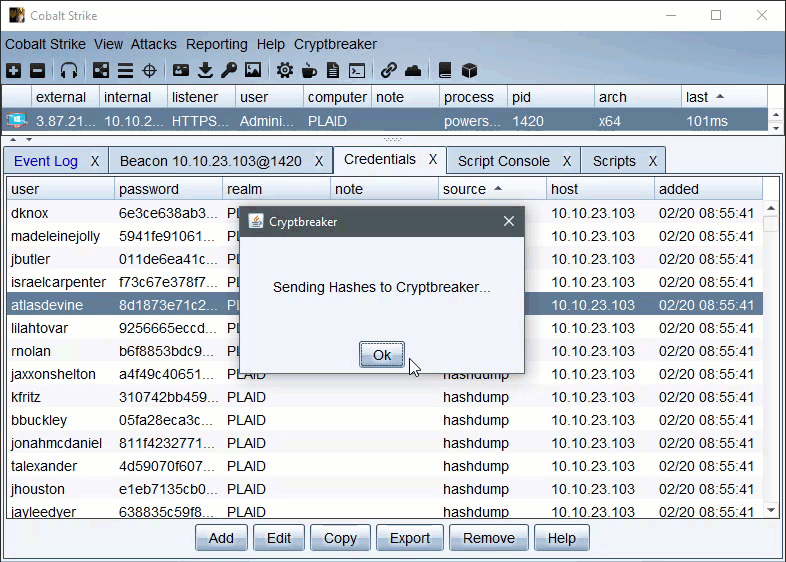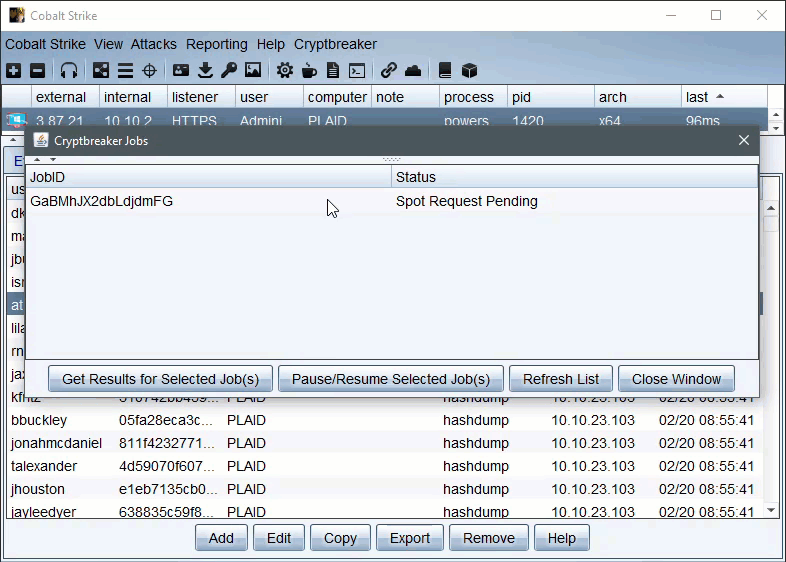
The aggressor script keeps track of what jobs it submitted and these jobs can be managed/viewed by the ‘Crack Jobs’ options of the main Cryptbreaker menu, Once a hash crack job shows completed in the Cryptbreaker ‘Crack Jobs’ menu you can retrieve the cracked hashes.
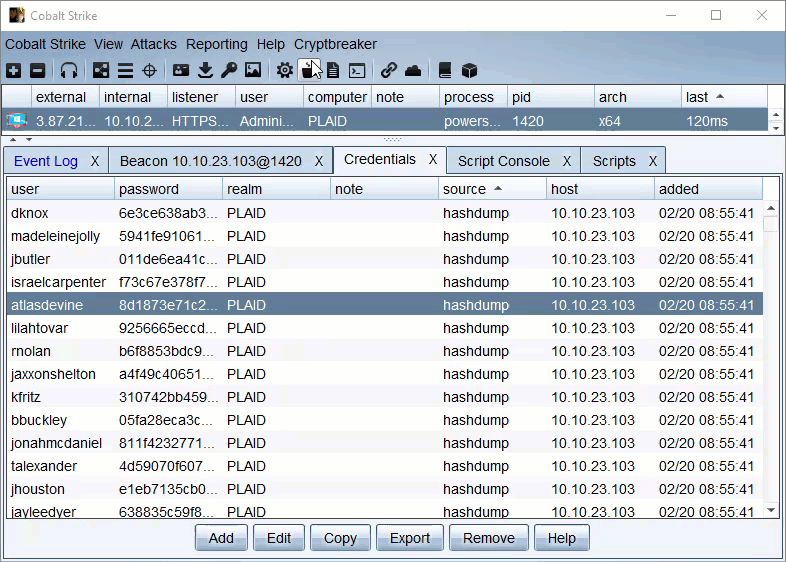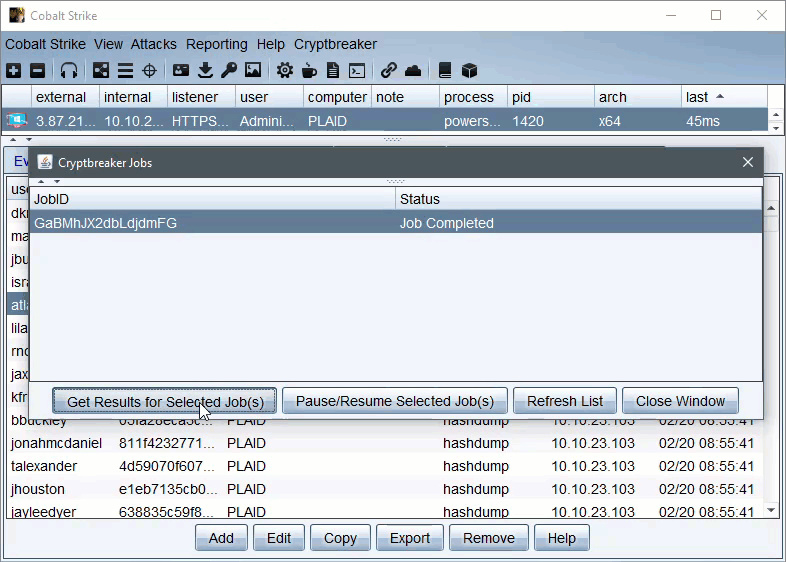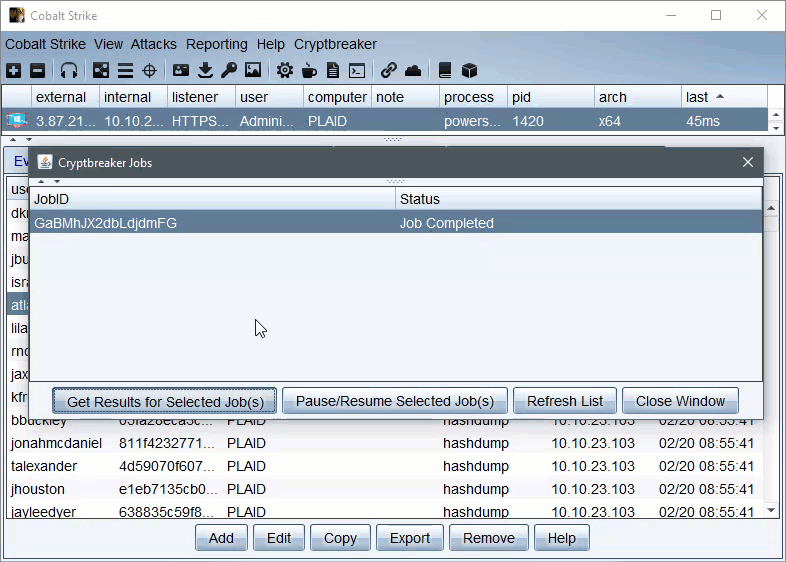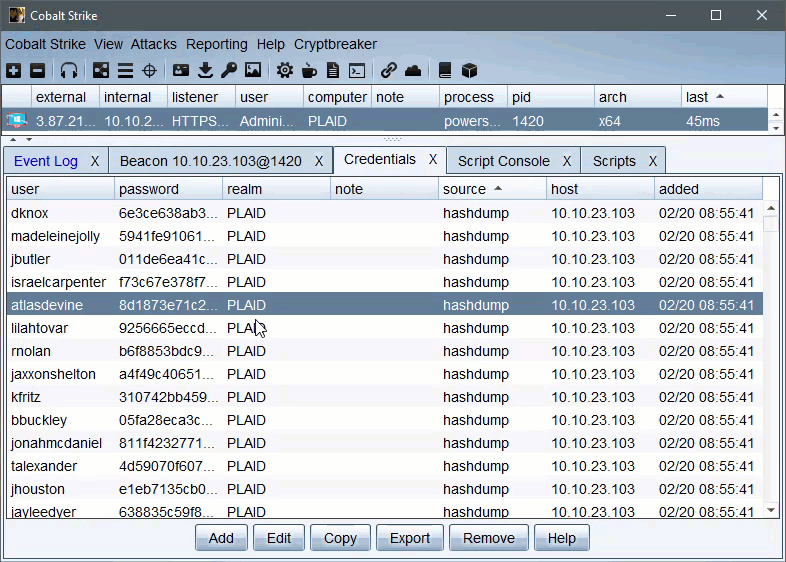
Credentials returned by Cryptbreaker aggressor script will be auto-added to the credentials table.
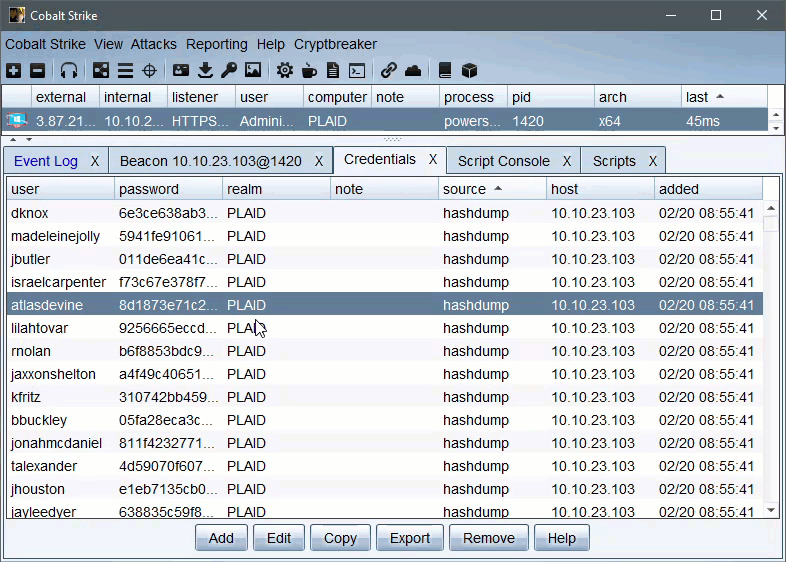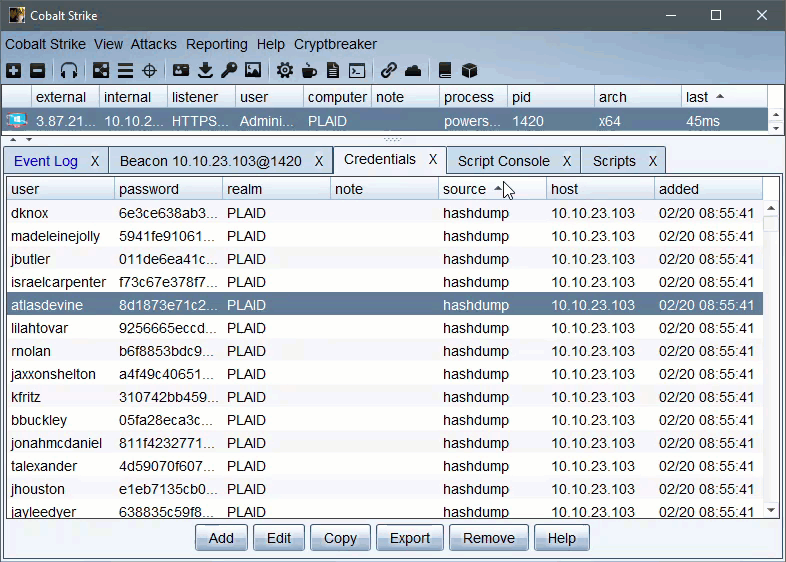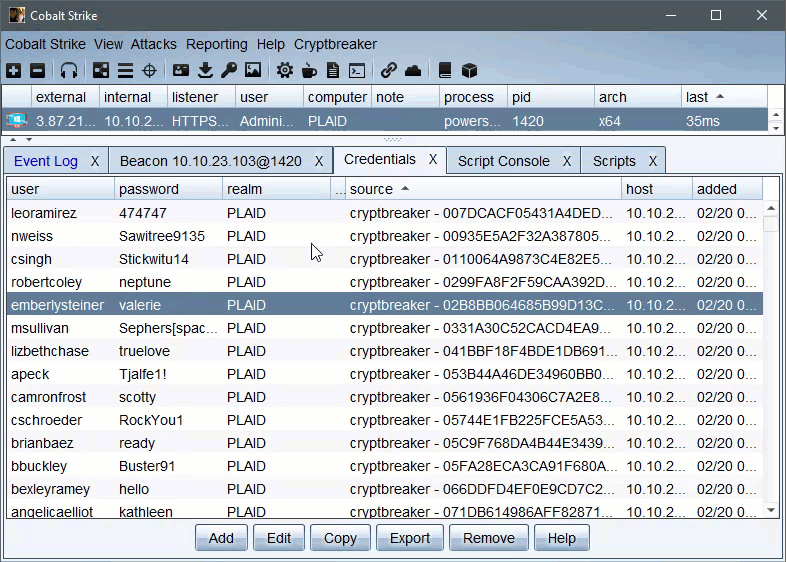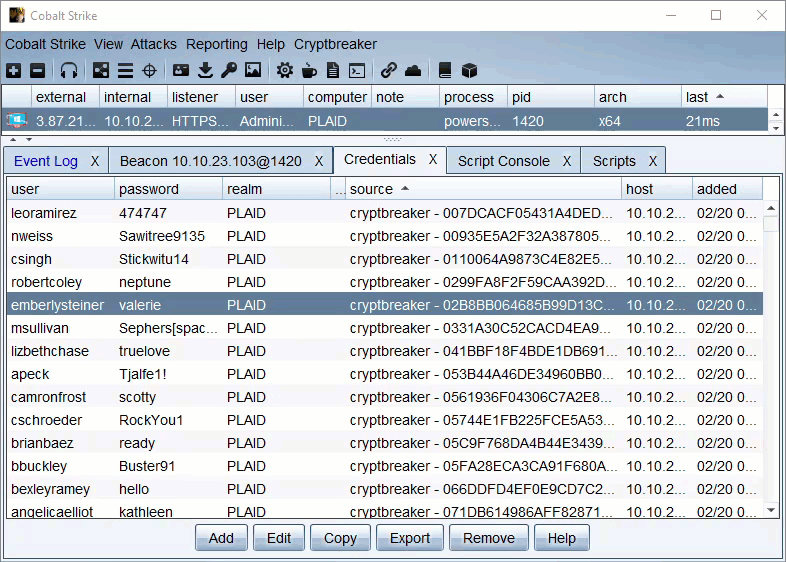
Cryptbreaker will return credentials with spaces replaced by [space]. When dealing with credentials containing [space] recomputing the hash via an NTLM hash calculator to be double sure of the content is recommended.
Invoke-Cryptbreaker.ps1
Not everyone uses Cobalt Strike and you might want an easy way to upload hashes recovered from some other tool like Empire or Responder. Using Responder as an example we can use the Invoke-Cryptbreaker.ps1 script that is also being released today to send recovered credentials to Cryptbreaker for cracking without leaving the comfort of our terminals. This script serves as a handy wrapper around the API endpoints published today.
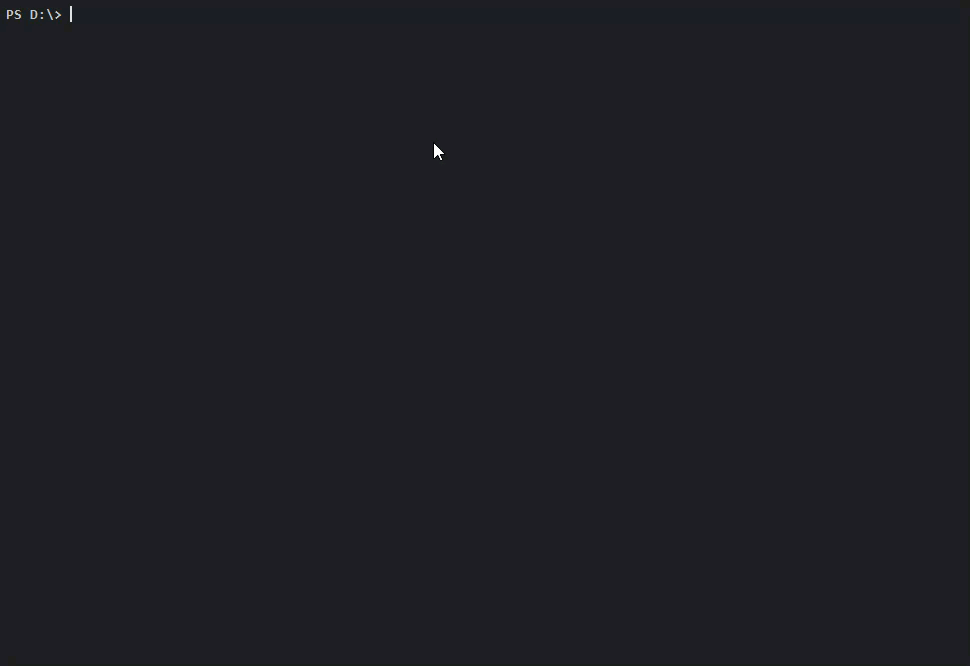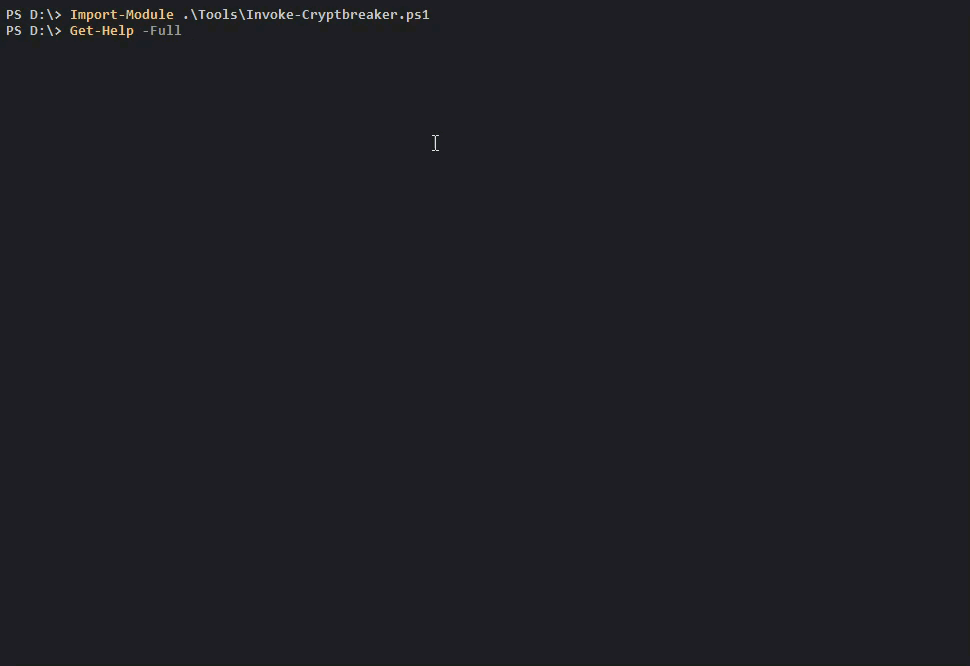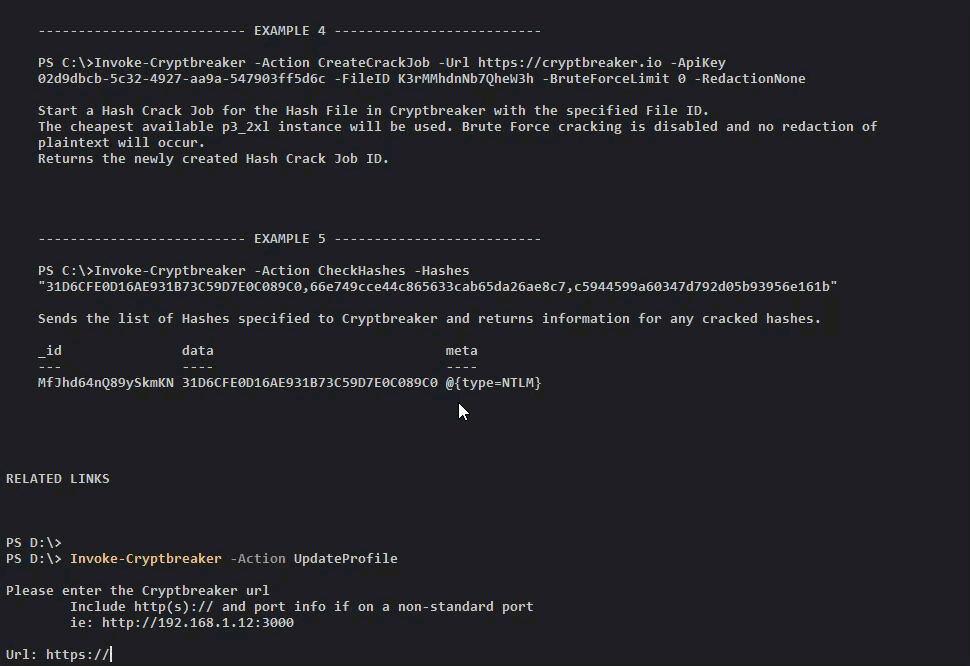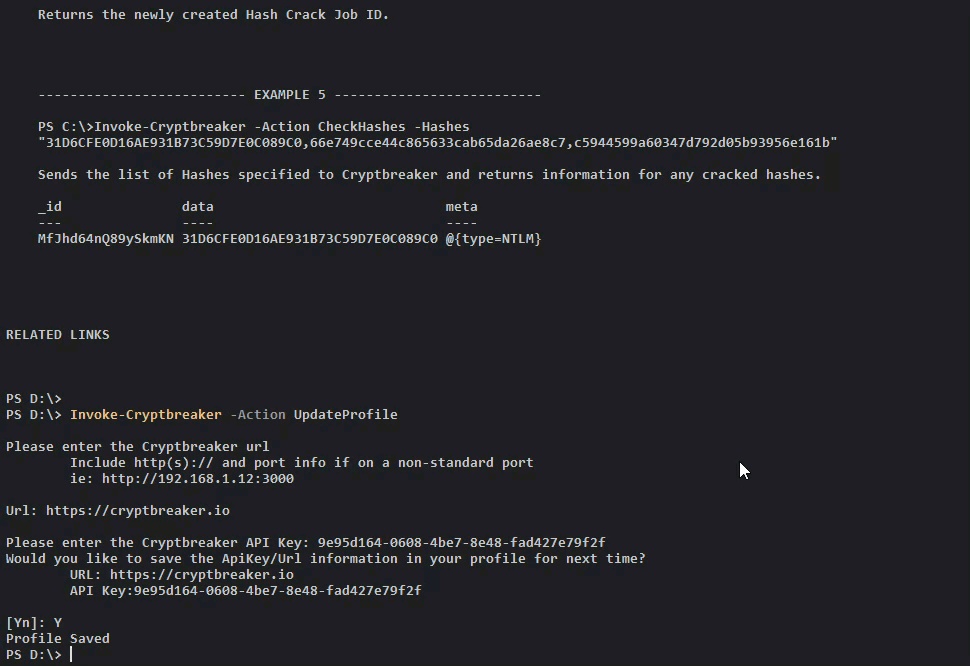
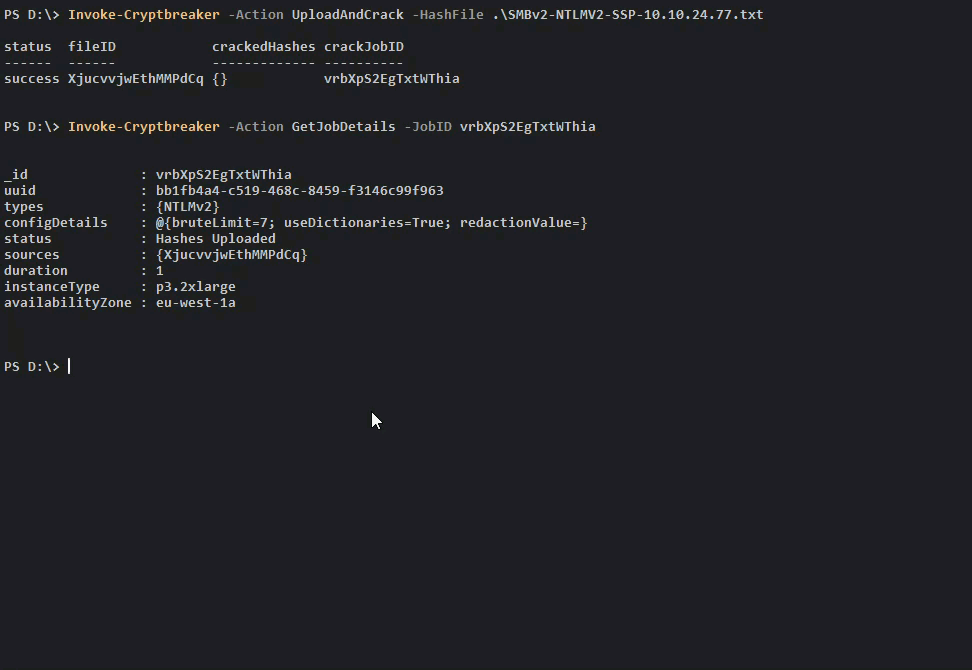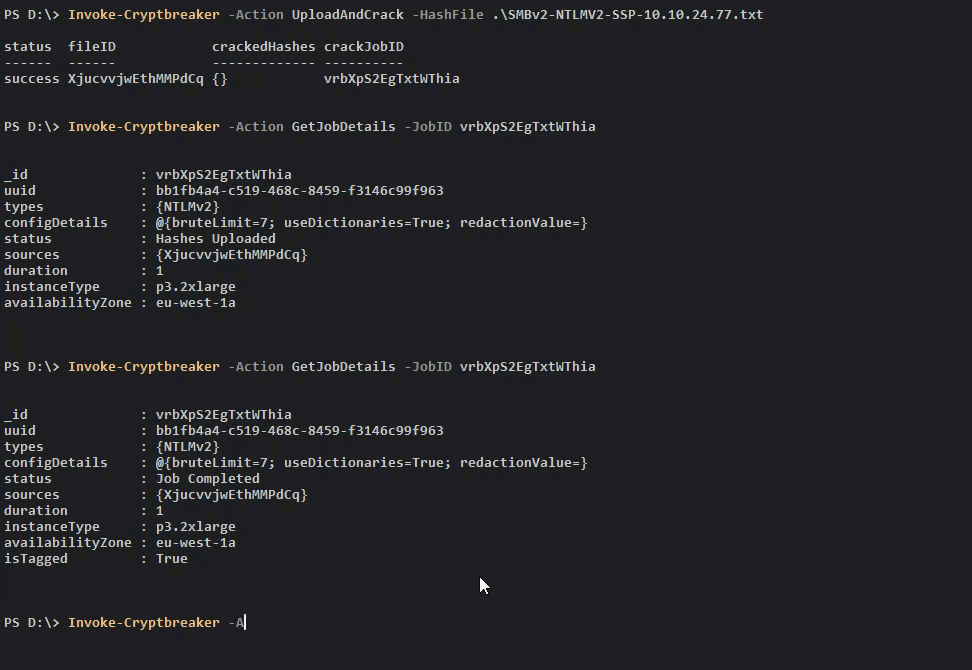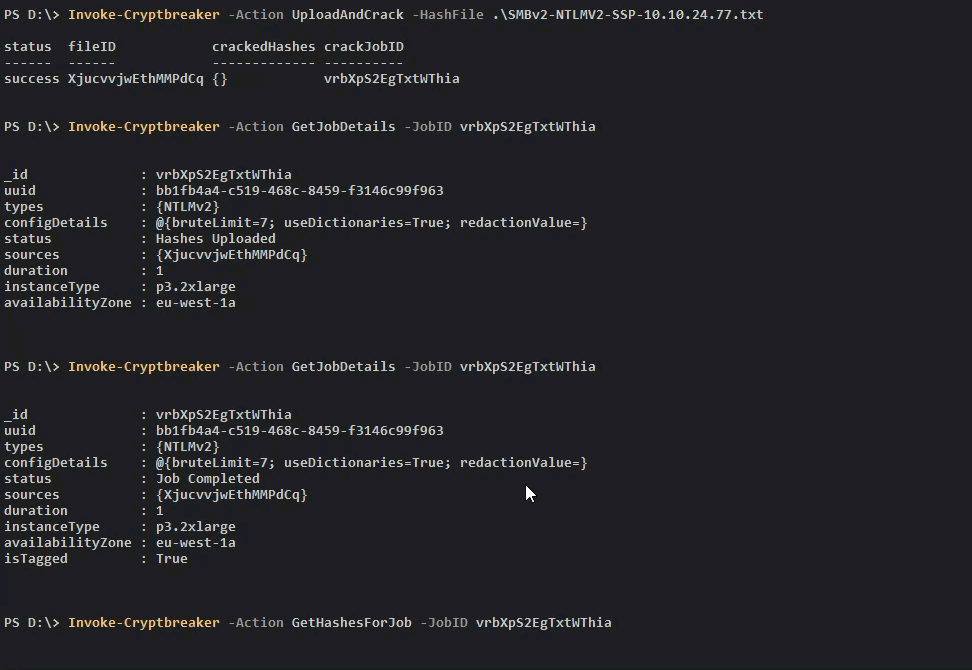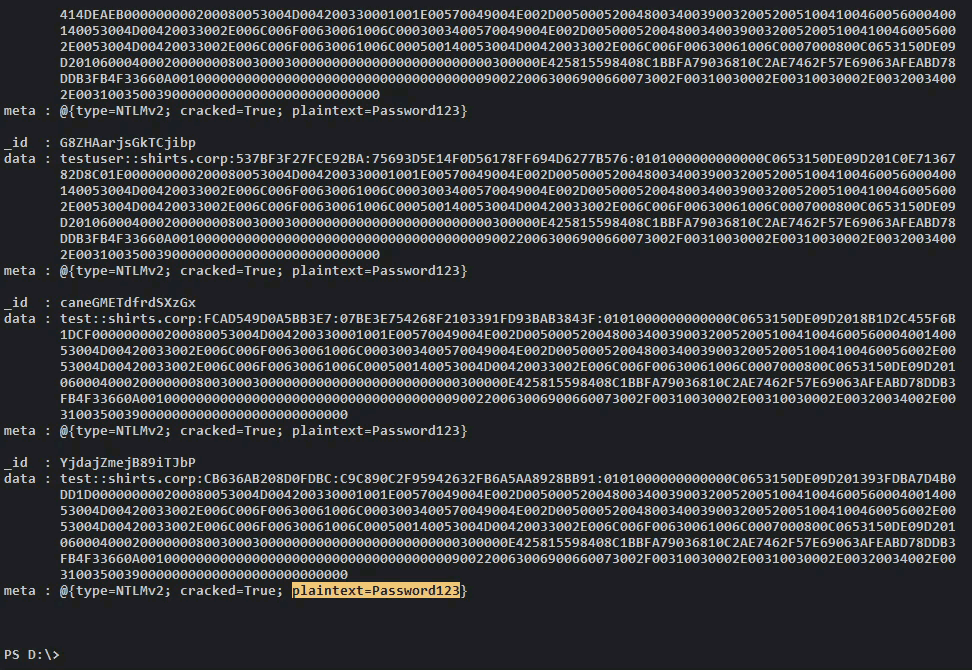
To upload and crack some NTLMv2 credentials captured by Responder we could do the following:
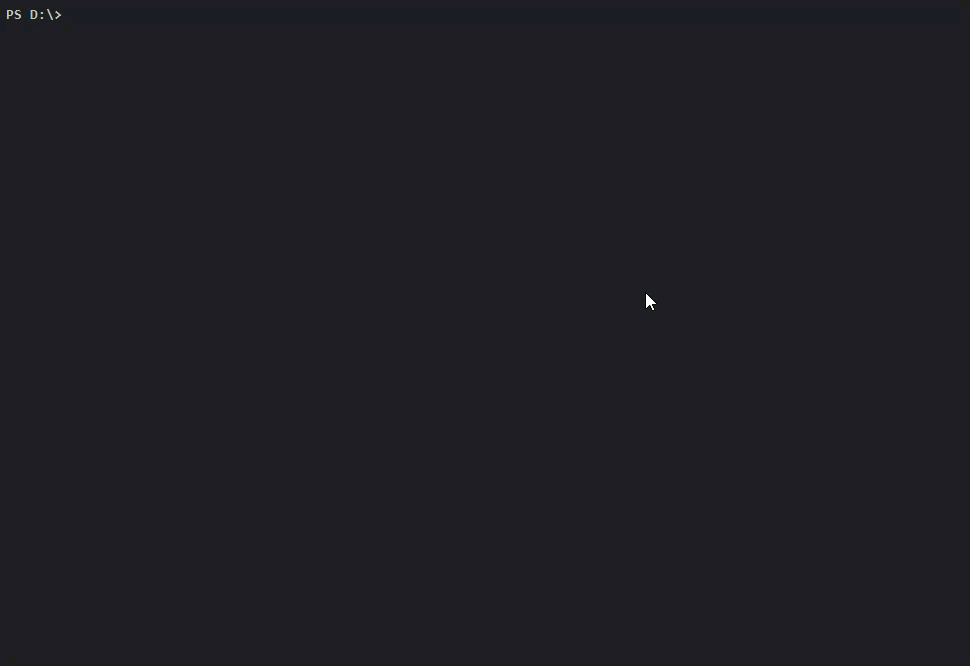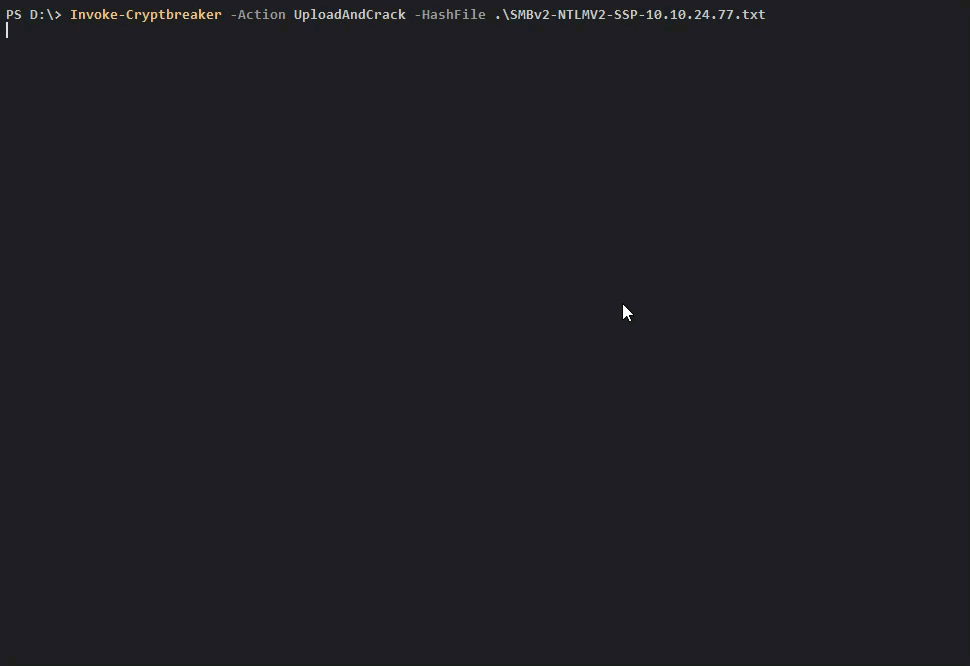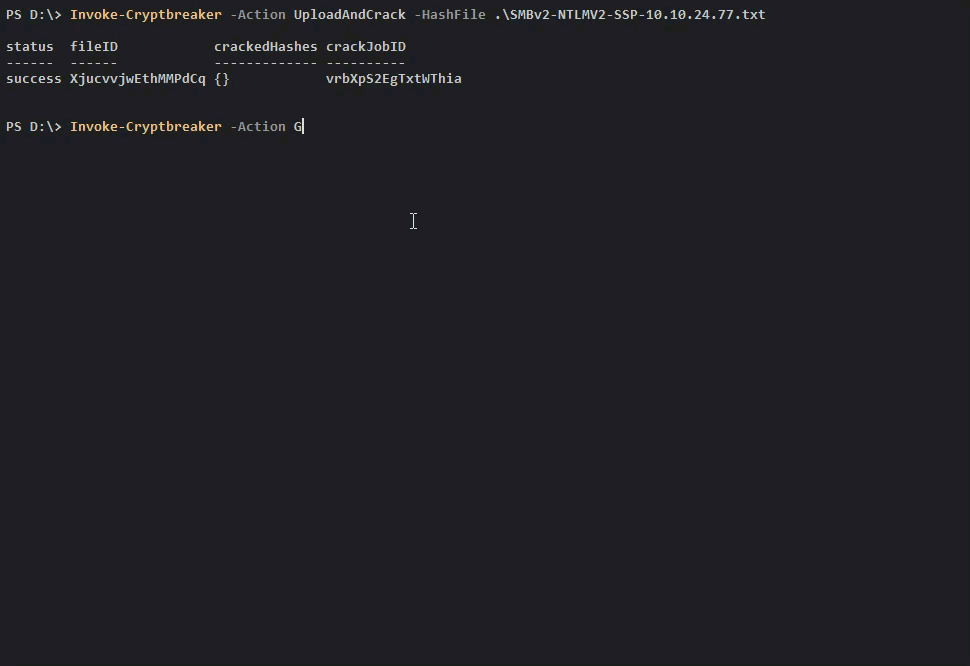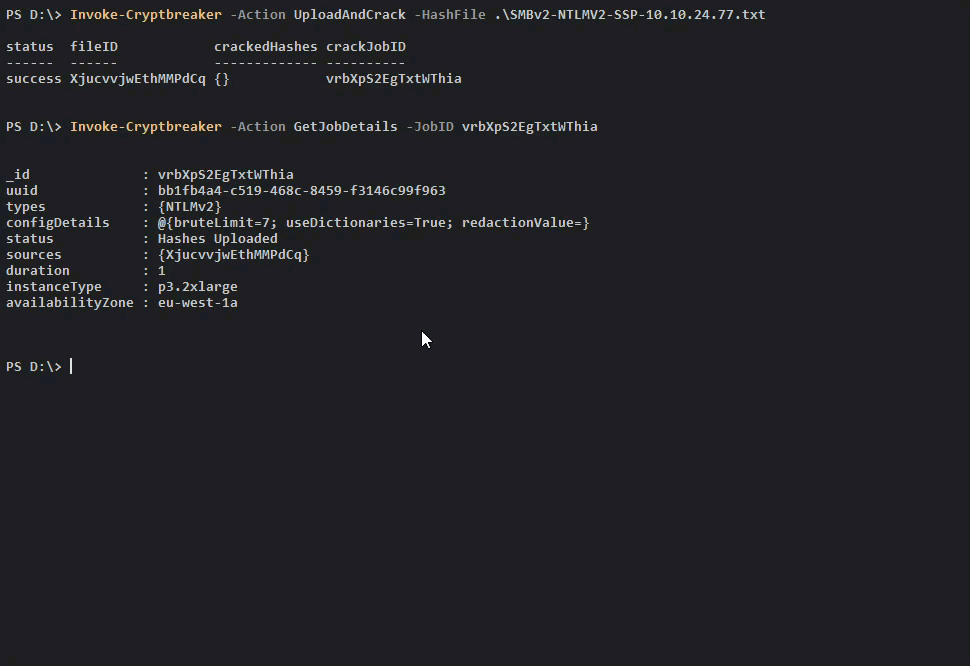
Once we check and see that the Cracking Job is complete we can retrieve our credentials.
Those are the main highlights for this release of Cryptbreaker!
Happy Hacking